我们知道使用 SSL(安全套接层)证书对于网站和在线服务来说非常重要,SSL 证书通过加密用户和服务器之间的通信,保护数据不被窃听或篡改。
本章节我们将介绍使用 Certbot 工具申请免费的 SSL 证书。
什么是 Certbot?
Certbot 是一个开源的自动化工具,用于获取和续订由 Let's Encrypt 提供的免费 SSL/TLS 证书。
Let's Encrypt 是一个由互联网安全研究小组(ISRG)运营的证书颁发机构(CA),它提供了一个自动化的流程来生成和更新证书,使得网站管理员可以轻松地为他们的站点启用 HTTPS 加密。
Certbot 的主要特点包括:
- 自动化:它可以自动验证域名所有权,并申请证书。
- 免费:它使用的是 Let's Encrypt 提供的免费证书。
- 兼容性:支持多种 web 服务器,如 Apache、Nginx 等。
- 易用性:提供了命令行界面,使得安装和使用变得简单。
- 续订:自动处理证书的续订,确保网站的 HTTPS 连接始终保持有效。
Let's Encrypt 颁发的证书有效期为 90 天,Certbot 会自动配置证书的续期任务,确保证书不会过期。
Certbot 安装
1. 在 Ubuntu/Debian 系统上安装 Certbot
使用 APT 安装:
sudo apt update sudo apt install certbot
安装完成后,Certbot 就可以用了。
安装 Snap 版本:
Snap 是 Certbot 官方推荐的安装方式,尤其是针对长期支持的 Ubuntu 版本。
sudo snap install core sudo snap refresh core sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot # 这一步是为了确保 certbot 命令能全局使用
2. 在 CentOS/RHEL 系统上安装 Certbot
安装 EPEL 仓库(适用于 CentOS 7 及以下):
sudo yum install epel-release
安装 Snap 版本:
sudo yum install snapd sudo systemctl enable --now snapd.socket sudo ln -s /var/lib/snapd/snap /snap snap --version # 查看snap 版本
Snap 安装 Certbot:
sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot # 这一步是为了确保 certbot 命令能全局使用
3. 在 macOS 上安装 Certbot
macOS 上可以使用 Homebrew 安装 Certbot:
brew install certbot
更多内容我们可以在 Certbot 网站 https://certbot.eff.org/ 查看各个系统平台的安装方法:

安装完成后,使用以下命令查看 certbot 安装的版本:
certbot --version
证书申请与续签
安装好certbot 后就可以使用以下命令来申请证书了,注意 *.runoops.com 为你自己的域名,需要修改:
certbot certonly -d *.runoops.com --manual --preferred-challenges dns --server https://acme-v02.api.letsencrypt.org/directory
执行以上命令后,填写信息:
[root@VM_0_15_centos certbostest]# certbot certonly -d *.runoops.com --manual --preferred-challenges dns --server https://acme -v02.api.letsencrypt.org/directory
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): xx@gmail.com # 这里输入你的邮箱
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.4-April-3-2024.pdf. You must agree in
order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y # 输入 Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y # 输入 Y
Account registered.
Requesting a certificate for *.runoops.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
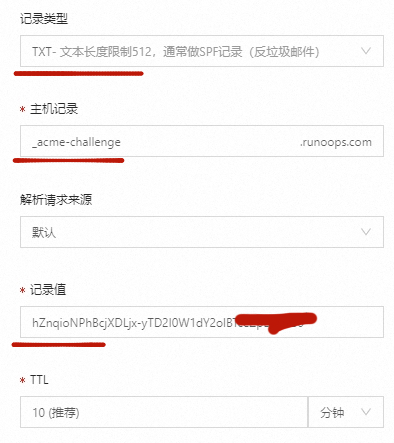
Please deploy a DNS TXT record under the name:
_acme-challenge.runoops.com. # 这里需要设置域名解析,需要到域名后台填写信息,参考下图
with the following value:
hZnqioNPhBcjXDLjx-yTD2I0W1dY2olBTceZpD5xxxx # 这里是域名解析的内容,参考下图
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.runoops.com.
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you've just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue # 参考下图设置完域名解析后,按回车就可以生成了,记住一定要先解析设置完成后再回车,然后生成的证书信息如下:
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/runoops.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/runoops.com/privkey.pem
This certificate expires on 2025-01-07.
These files will be updated when the certificate renews.
NEXT STEPS:
- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an n hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot c the certificate's expiry date.
We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can tr by visiting https://act.eff.org.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -设置域名解析用于验证证书:
Let's Encrypt 颁发的证书有效期为 90 天,可以使用以下命令进行续签证书:
certbot certonly --force-renewal --manual -d '*.runoops.com' \
--preferred-challenges dns \
--server https://acme-v02.api.letsencrypt.org/directory执行以上续签命令后,就会让我们更新下 DNS 解析记录:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Requesting a certificate for *.runoops.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name:
_acme-challenge.runoops.com.
with the following value:
hZnqioNPhBcjXDLjx-yTD2I0W1dY2olBTceZpD5xxxx # 这里会显示你要更改的 DNS 解析记录值,设置好就可以完成更新了
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.runoops.com.
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you've just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -其它
可能的报错:
[root@VM_0_15_centos ~]# snap install --classic certbot
error: cannot communicate with server: Post "http://localhost/v2/snaps/certbot": dial unix /run/snapd.socket: connect: no such file or directory解决:
systemctl restart snapd.service 自学教程
自学教程
分享笔记